Understanding SSL/TLS: From Certificates to Vulnerabilities
By suktech24, written on Sun 1 Sep 2024, Estimated reading time : 10-12 mins
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are critical protocols in establishing secure connections across networks. These protocols ensure data privacy, integrity, and authentication, safeguarding communications between clients and servers. Digital certificates are at the heart of SSL/TLS protocols, issued by Certificate Authorities (CAs). These certificates are essential for verifying the identities of systems and facilitating secure connections. Public Key Infrastructure (PKI) and cryptographic technologies like SHA-256 work together to ensure encrypted communication, message integrity, and secure authentication processes.
This blog post explores SSL/TLS certificates, their associated fields, and the role of these protocols in supporting the confidentiality, integrity, and availability (CIA) triad and examples of SSL/TLS vulnerabilities and brief information of detection and MITRE ATT&CK framework coverage for threat modeling.
- SSL and TLS
- 1.1. What is SSL and TLS?
- 1.2. OSI Layer of TLS/SSL
- SSL/TLS Certificate Field Names
- SSL/TLS Protocol Stack
- SSL/TLS and how it supports CIA triad
- 4.1. What is CIA Triad?
- 4.2. SSL/TLS – how it supports CIA triad
- SSL/TLS Common Vulnerabilities and Exposures (CVE)
1. SSL and TLS
1.1. What is SSL and TLS?
Secure Sockets Layer (SSL) protocol was developed by Netscape Communications Corporation. SSL ensures the data that is transferred between a client and a server remains private.
- This protocol enables the client to authenticate the identity of the server. When your server has a digital certificate, SSL-enabled browsers can communicate securely (encrypted communication) with your server, using SSL. It prevents hackers from seeing or stealing any information transferred, including personal or financial data.
- However, SSL is an older technology that contains some security flaws.
- TLS is the direct successor to SSL, and all versions of SSL are now deprecated. However, it’s common to find the term SSL describing a TLS connection.
1.2 OSI Layer of TLS/SSL
With regard to the OSI (Open Systems Interconnection) model, the TLS/SSL protocols are situated in the presentation layer. Below diagram illustrates how SSL/TLS fits into OSI and TCP/IP models.
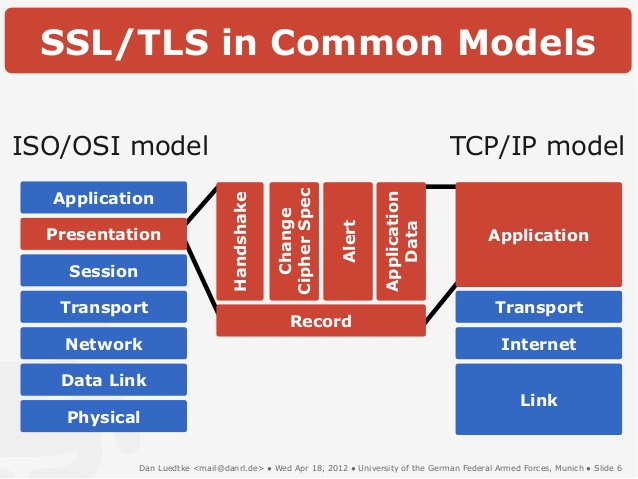
Sourced from , https://security.stackexchange.com/questions/195229/where-exactly-in-the-osi-model-does-tls-ssl-belong
2. SSL/TLS Certificate Field Names
An SSL/TLS certificate is a digital object that allows systems to verify the identity & subsequently establish an encrypted network connection to another system using the Secure Sockets Layer/Transport Layer Security (SSL/TLS) protocol.
Before diving into SSL/TLS protocol stack, let’s have a look at terminologies that are of importance to understand the protocols. To check what fields are included in the Certifciate Viewer, go to the website you want to visit. And then Click on 1. If you hover over it, it says “view site information. After you click on it, you will see, “Connection is secure”. Click forward arrow >.
After you click on Connection is secure, you will see below. Click on Certificate is valid.
- CA (Certificate Authority)
- A certificate authority is a company or organization that acts to validate the identities of entities (such as websites, email addresses, companies, or individual persons) and bind them to cryptographic keys through the issuance of electronic documents known as digital certificates.
- Distinguished Name information – A distinguished name is used to provide an identity in a specific context.
- CN (Common Name)
- Name being certified
- e.g. *.apache.org, aws.amazon.com, *.google.com
- O (Organization or Company)
- For this, you might see <Not Part Of Certificate>
- OU (Organisational Unit)
- Name is associated with this organization unit, such as a department
- For this, you might see <Not Part Of Certificate>
- CN (Common Name)
- Public key infrastructure (PKI)

- Sourced from, https://www.researchgate.net/figure/Public-Key-Infrastructure-AppViewX-2020_fig1_351247755
- It refers to the deployment and management of a public key encryption system.
- The core technology that enables PKI is public key cryptography, also known as asymmetric encryption. Asymmetric encryption is used to create a public key, pair it with a private key, and create an association between the two. Plain text is encrypted and converted to ciphertext by an encryption key. Once the data is delivered to the recipient, the decryption key is used to decrypt the ciphertext back to plain text so they can read the original message, confident that it hasn’t been compromised.
- Public keys are discoverable. Hence, you can see them in the certificate. They are published and are not strictly controlled. The private key however, is known only by its owner. Public keys are paired with an associated private key by generating random numeric combinations of variable length, which makes it difficult for hackers to crack them using brute-force attacks.
- PKI’s authentication and key-exchange mechanisms enable security functionality such as access control, secure messaging, data encryption, data/message signing, secure boot, and more.
- SHA-256 Fingerprints
- SHA stands for Secure Hash Algorithm.
- SHA-256 is a part of the SHA-2 algorithm family. The “256” in SHA-256 signifies its fixed hash digest size, always producing a 256-bit value, regardless of the input plaintext or cleartext size. This characteristic ensures consistent and strong cryptographic hashing.
- There are many applications of SHA-256. In this case, it is used with public-key cryptography to create digital signatures. It allows for the verification of the integrity and authenticity of digital messages or documents.
- SHA-256 ensures data remains unchanged during transmission.
3. SSL/TLS Protocol Stack
The SSL protocol consists of two layers of protocols: the SSL record protocol at the lower layer and the SSL handshake protocol, change cipher spec protocol, and alert protocol at the upper layer.
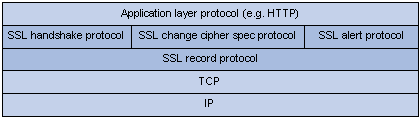
sourced from , https://support.hpe.com/techhub/eginfolib/networking/docs/routers/msrv5/cg/5200-2323_security-cg/content/459369550.htm
- SSL Handshake protocol
- Negotiates the cipher suite to be used for secure communication (including the symmetric encryption algorithm, key exchange algorithm, and MAC algorithm), securely exchanges the key between the server and client, and implements identity authentication of the server and client. Through the SSL handshake protocol, a session is established between a client and the server. A session consists of a set of parameters, including the session ID, peer certificate, cipher suite, and master secret.
- Change Cipher Spec(CCS) Protocol
- It is a critical component within the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) frameworks, which are designed to provide secure communication over a computer network. The primary function is to signal the transition from the initial unencrypted state to an encrypted state using the negotiated cryptographic parameters. This transition is important for ensuring that the communication between client and server is secured and protected from eavesdropping and tampering.
- Alert Protocol
- Enables the SSL client and server to send alert messages to each other. An alert message contains the alert severity level and a description.
- Record Protocol
- Fragments data to be transmitted, computes and adds MAC to the data, and encrypts the data before transmitting it to the peer end.
- What is Cipher Suite?
- Cipher suites are named combinations of cryptographic algorithms that help secure the connection. Choosing the right cipher suites is crucial for ensuring optimal security and performance
- The SSL handshake protocol determines how the client and server negotiate which cipher suites they will use.
- Cipher suites are sets of encryption algorithms that secure communications between clients and servers.
- They specify cryptographic algorithms like symmetric ciphers, message authentication codes, key exchange methods etc.
- Proper cipher suite configuration is critical for security, compatibility and performance.
- Cipher Suite four algorithms
- It contains four algorithms – key exchange, encryption, message authentication, and hash functions.
- Key exchange: Allows the server and client to securely exchange keys used for encryption and decryption of data. Common key exchange algorithms include RSA, DHE, ECDHE, RSA_PSK.
- Encryption: Symmetric encryption cipher used to encrypt messages after key exchange. AES, RC4, 3DES, Data Encryption Standard,
- Message Authentication: Message Authentication Code (MAC) algorithm to ensure message integrity and authenticity. HMAC-SHA1, SHA256 are examples.
- Hash: Cryptographic hash functions used by other algorithms. MD5, SHA1 and SHA256 are commonly used hashes.
- SHA256 – SHA256 is a stronger alternative hash algorithm supported in modern ciphers.
- MD5 – Message Digest algorithm 5 produces a 128‐bit hash value. MD5 is considered insecure and not recommended.
- Sequences of SSL handshake sequence.

sourced from, https://my.f5.com/manage/s/article/K15292

Source from , https://www3.ntu.edu.sg/home/ehchua/Programming/webprogramming/HTTP_SSL.html
4. SSL/TLS and how it supports CIA triad
4.1. What is CIA Triad?
The three letters in “CIA triad” stand for Confidentiality, Integrity, and Availability. The CIA triad is a guiding model that forms the basis for the development of security systems.

Sourced from, https://www.f5.com/labs/learning-center/what-is-the-cia-triad
- Confidentiality – preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information
- Integrity – guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity
- Availability – ensuring timely and reliable access to and use of information
4.2. SSL/TLS – how it supports CIA triad
A digital certificate provides:
- Authentication, by serving as a credential to validate the identity of the entity that it is issued to.
- Encryption, for secure communication over insecure networks such as the internet.
- Integrity of documents signed with the certificate so that they cannot be altered by a third party in transit.
As you can see,
- Certificate authentication supports Confidentiality and Integrity of CIA triad.
- Encryption supports for maintaining confidentiality. Even if the data get intercepted by a malicious unauthorized party, they will not be able to understand since the contents are encrypted.
- Integrity supports Integrity of CIA triad.
5. SSL/TLS Common Vulnerabilities and Exposures (CVE)
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that’s been assigned a CVE ID number.
You can search for CVE on cve.org website. Below are the examples of SSL/TLS certificate related CVE. The descriptions are copied from cve.mitre.org website.
CVE Examples
CVE-2022-45453 – TLS/SSL weak cipher suites enabled. The following products are affected: Acronis Cyber Protect 15 (Windows, Linux) before build 30984.
CVE-2023-40464 – Several versions of ALEOS, including ALEOS 4.16.0, use a hardcoded SSL certificate and private key. An attacker with access to these items could potentially perform a man in the middle attack between the ACEManager client and ACEManager server.
CVE-2024-37015 – An issue was discovered in Ada Web Server 20.0. When configured to use SSL (which is not the default setting), the SSL/TLS used to establish connections to external services is done without proper hostname validation. This is exploitable by man-in-the-middle attackers.
CVE 2014-0224 – SSL/TLS MITM vulnerability – An attacker using a carefully crafted handshake can force the use of weak keying material in OpenSSL SSL/TLS clients and servers. This can be exploited by a Man-in-the-middle (MITM) attack where the attacker can decrypt and modify traffic from the attacked client and server. The attack can only be performed between a vulnerable client *and* server.
- https://access.redhat.com/solutions/905793
- https://beaglesecurity.com/blog/vulnerability/processing-change-cipher-spec.html
Detections
The followings could be used to detect if any malicious actors attempt to exploit these types of vulnerabilities (They are not exhausted list):
- Monitor network traffic for connections using weak cipher suites. In detection, check for weak cipher algorithms
- Write detection to detect any anomalies
Also make sure to use MITRE ATT&ACK to understand adversary behavior since it helps mapping out the various stages of an attack, from initial access to data exfiltration. It also provides as a guide for red/blue/purple teaming exercises, ensuring comprehensive coverage of potential SSL/TLS attack vectors.
6. Summary
I hope that this blog highlights the importance of understanding what these protocols are, how it works, what it involves. Understanding them enable you to detect and mitigate potential security threats, especially with SSL/TLS-related vulnerabilities such as weak cipher suites or improper hostname validation, as outlined by CVEs.
Below is the summary keypoints:
- SSL and TLS
- SSL: Older protocol for secure data transfer between client and server
- TLS: Upgraded version of SSL, fixing vulnerabilities
- Both operate in the presentation layer of the OSI model
- SSL/TLS Certificate Field Names
- Common Name (CN): Identifies the secured domain
- Organization (O) and Organizational Unit (OU): Provide entity details
- Public Key Infrastructure (PKI): Manages public key encryption
- SHA-256 Fingerprint: Ensures data integrity
- SSL/TLS Protocol Stack
- Consists of Record Protocol, Handshake Protocol, Change Cipher Spec (CCS) Protocol, and Alert Protocol
- Cipher Suite: Combination of cryptographic algorithms for secure connections
- SSL/TLS and CIA Triad
- Confidentiality: Encryption prevents unauthorized access
- Integrity: Digital signatures ensure data hasn’t been altered
- Availability: Indirectly supported through secure access mechanisms
- Common Vulnerabilities and Exposures (CVE)
- CVE-2022-45453: Weak cipher suites in Acronis Cyber Protect
- CVE-2023-40464: Hardcoded SSL certificate in ALEOS
- CVE-2024-37015: Improper hostname validation in Ada Web Server
- Setup detection. Use mitre attack framework for threat modeling, detection guidance and red/blue/purple team exercises.
References
These articles are recommended to read first for further details information.
- HTTP Security with SSL, https://www3.ntu.edu.sg/home/ehchua/Programming/webprogramming/HTTP_SSL.html
- Transport Layer Security (TLS), https://hpbn.co/transport-layer-security-tls/
- SSL/TLS Strong Encryption: An Introduction, https://httpd.apache.org/docs/current/ssl/ssl_intro.html
- What Is An SSL/TLS Certificate?, https://aws.amazon.com/what-is/ssl-certificate/
Referenced Articles
- CVE examples
- Data Integrity: Detecting and Responding to Ransomware and Other Destructive Events, https://www.nccoe.nist.gov/publication/1800-26/VolA/index.html
- K15292: Troubleshooting SSL/TLS handshake failures, https://my.f5.com/manage/s/article/K15292
- Mitre ATT&CK Matrix for Enterprise, https://attack.mitre.org/
- Secure Sockets Layer (SSL) protocol, https://www.ibm.com/docs/en/ibm-http-server/9.0.5?topic=communications-secure-sockets-layer-ssl-protocol
- SSL Glossary, https://www.digicert.com/what-is-ssl-tls-and-https
- What’s the difference between SSL and TLS?, https://aws.amazon.com/compare/the-difference-between-ssl-and-tls/
- Where exactly in the OSI model does TLS/SSL belong [duplicate], https://security.stackexchange.com/questions/195229/where-exactly-in-the-osi-model-does-tls-ssl-belong
- What is the CIA Triad?, https://www.fortinet.com/resources/cyberglossary/cia-triad
- What is a Certificate Authority (CA)?, https://www.ssl.com/article/what-is-a-certificate-authority-ca/
- What is public key infrastructure, https://www.hashicorp.com/blog/what-is-public-key-infrastructure-pki
- What are SSL Cipher Suites and Everything You Need To Know, https://sslinsights.com/what-are-ssl-cipher-suites/


Leave a comment