By suktech24, written on Sat 21 Sep 2024, Estimated reading time : 20-25 mins
Cybersecurity solutions evolve alongside the growing complexity in software, vulnerabilities in software packages, dependencies (open source libraries and third party packages), different endpoint devices , complex networks (onprem, hybrid, cloud, aws, azure, gcp multi-cloud environments) , increased attack surfaces, rise of sophisticated cyber attacks (advanced tactics, techniques) and the needs for automation in incident responses.
When I first started my career in Cybersecurity, I found there are many abbreviations used for various technology solutions-like – SIEM, EDR, XDR, SOAR, XSOAR, and XSIAM-confusing. At the start, it was not clear to me on what each solution was and what problem each of them solved, and how they differed from one another, their history or how they evolved. It took me a while to understand each of them. In this blog post, I want to demystify each technology solution, differentiate amongst them and what specific problems they solve. Information are sourced and extracted from Crowdstrike, PaltoAlto, SentinelOne, Sysdig, Splunk and other websites.
The followings will be covered:
- SIEM (Security Information and Event Management)
- EDR (Endpoint Detection and Response)
- XDR (Extended Detection and Response)
- EDR vs XDR
- MDR (Managed Detection and Response)
- SOAR (Security Orchestration, Automation and Response)
- SIM vs SOAR
- XSOAR (Extended Security Orchestration, Automation, and Response)
- XSIAM (Extended Security Intelligence and Automation Management)
1. SIEM (Security Information and Event Management)
- What is it?
- Security information and event management (SIEM) is a set of tools and services that combine security events management (SEM) and security information management (SIM) capabilities that helps organizations recognize potential security threats and vulnerabilities before business disruptions occur. SIM focuses on collecting and managing logs and other security data while SEM involves real-time analysis and reporting.
- SIEMs provide visibility into malicious activity by pulling data from every corner of an environment and aggregating it in a single centralized platform, where it can be used to qualify alerts, create reports and support incident response. The ability to analyze data from all network applications and hardware at any time helps organizations recognize potential security threats before they have a chance to disrupt business operations.
- How it works?
- A SIEM works by collecting log and event data from an organization’s applications, servers, security devices and systems into a centralized platform. Then, a SIEM will sort this data into categories and analyze it for deviations against behavioral rules defined by your organization’s IT teams to identify potential threats. For example, SIEM may categorize deviations into “malware activity” or “failed logins.” Deviations will prompt the system to alert security or IT analysts to further investigate the unusual activity.
- Limitations
- SIEMs cannot always provide complete context on unstructured data. This can lead to false alerts, and security teams can find it difficult to diagnose and research security events because of the high volume of alerts and data provided by the SIEM.
- Responses to alerts can be delayed or overlooked because analysts lack an understanding of which alerts need attention. SIEMs do not replace enterprise security controls such as intrusion prevention systems, firewalls or antivirus technologies. The SIEM itself does NOT monitor events as they happen throughout the enterprise in real time, but rather uses log data recorded by other software to determine that an event occurred.
2. EDR (Endpoint Detection and Response)
- What it is?
- EDR (endpoint detection and response) continuously monitors endpoints (desktops, laptops, servers, or any device connected to an organization’s network) to detect malicious behavior or malware. As the name implies, EDR systems help users respond to threats; with some tools, this process is automated.
- EDR is often referred to as a natural evolution of antivirus software because both tools perform similar functions. Traditional antivirus, however, typically relies on signature-based detection to spot known threats. EDR uses behavior-based detection to detect emerging attacks such as advanced persistent threats (APTs) and fileless malware, whereas traditional antivirus typically does not. EDR software, however, can be a component of next-generation antivirus products.
- EDR security solutions record the activities and events taking place on endpoints and all workloads, providing security teams with the visibility they need to uncover incidents that would otherwise remain invisible. An EDR solution needs to provide continuous and comprehensive visibility into what is happening on endpoints in real time.
- An EDR tool should offer advanced threat detection, investigation and response capabilities — including incident data search and investigation alert triage, suspicious activity validation, threat hunting, and malicious activity detection and containment.
- Coined by Gartner’s Anton Chuvakin, EDR is defined as a solution that “records and stores endpoint-system-level behaviors, uses various data analytics techniques to detect suspicious system behavior, provides contextual information, blocks malicious activity, and provides remediation suggestions to restore affected systems.”
- How it works?
- EDR solutions are designed to provide real-time threat intelligence, automated incident response, and forensic investigation capabilities. EDR tools allow security teams to detect and respond to advanced threats quickly and efficiently, minimizing the risk of data breaches and other cybersecurity incidents.
- Cyberattacks like malware, ransomware, and phishing attacks often target endpoints to gain access to sensitive data or to launch further attacks.
- Endpoint security solutions play a crucial role in endpoint security by providing real-time threat detection and response capabilities.
- Imagine a scenario where an organization deploys EDR software on all employee laptops. If an endpoint detects suspicious activity like an unauthorized process running, EDR can isolate the endpoint from the network, collect forensic data, and trigger an alert to the security team.
- Six key aspects of EDR
- Endpoint visibility : Real-time visibility across all your endpoints allows you to view adversary activities, even as they attempt to breach your environment, and stop them immediately.
- Threat database : Effective EDR requires massive amounts of telemetry collected from endpoints and enriched with context so it can be mined for signs of attack with a variety of analytic techniques.
- Behavioral protection : Relying solely on signature-based methods or indicators of compromise (IOCs) lead to the “silent failure” that allows data breaches to occur. Effective endpoint detection and response requires behavioral approaches that search for indicators of attack (IOAs), so you are alerted of suspicious activities before a compromise can occur.
- Insight and intelligence : An endpoint detection and response solution that integrates threat intelligence can provide context, including details on the attributed adversary that is attacking you or other information about the attack.
- Fast response : EDR that enables a fast and accurate response to incidents can stop an attack before it becomes a breach and allow your organization to get back to business quickly.
- Cloud-based solution : Having a cloud-based endpoint detection and response solution is the only way to ensure zero impact on endpoints, while making sure capabilities such as search, analysis and investigation can be done accurately and in real time.
- Limitations
- Despite its strengths, EDR faces limitations. High volumes of alerts can overwhelm security teams, leading to alert fatigue and potential oversight of critical threats. False positives remain a challenge, consuming valuable time and resources.
- EDR solutions also require significant expertise to manage and interpret complex data, which can strain smaller organizations needing more specialized staff. Additionally, sophisticated attackers may employ evasion techniques that bypass EDR detection, exploiting zero-day vulnerabilities or using encrypted channels.
- While EDR enhances security, it is not a standalone solution and must be integrated with other security measures to ensure comprehensive protection.
- Examples
- Cloud: CrowdStrike Falcon
- On-Premises: Symantec Endpoint Detection and Response
3. XDR (Extended Detection and Response)
- What it is?
- XDR is a relatively new cybersecurity concept that was developed to help IT professionals sort through the flood of security alerts and detect threats more quickly. The inadequacies of traditional security technologies, which were unable to detect and respond to complex threats across multiple vectors, prompted the need for XDR.
- In today’s cybersecurity environment, XDR is recognized as a critical technique for providing adequate coverage against complex threats. XDR was created to provide a comprehensive security system that can detect and respond to attacks from a variety of vectors, including the cloud, network, and email.
- From a single console, it provides improved cross-domain threat hunting and forensic investigation capabilities.
- Extended detection and response (XDR) collects threat data from previously siloed security tools across an organization’s technology stack for easier and faster investigation, threat hunting, and response. An XDR platform can collect security telemetry from endpoints, cloud workloads, network email, and more.
- Gartner defines XDR as a “unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.”
- With all of this enriched threat data filtered and condensed into a single console, XDR enables security teams to rapidly and efficiently hunt and eliminate security threats across multiple domains from one unified solution.
- How it works?
- XDR connects data from siloed security solutions so they can work together to improve threat visibility and reduce the length of time required to identify and respond to an attack. XDR enables advanced forensic investigation and threat hunting capabilities across multiple domains from a single console.
- Here’s a simple step-by-step of how XDR works:
- Step 1. Ingest: Ingest and normalize volumes of data from endpoints, cloud workloads, identity, email, network traffic, virtual containers and more.
- Step 2. Detect: Parse and correlate data to automatically detect stealthy threats with advanced artificial intelligence (AI) and machine learning (ML).
- Step 3 Respond: Prioritize threat data by severity so that threat hunters can quickly analyze and triage new events, and automate investigation and response activities.

- Image from, https://www.crowdstrike.com/cybersecurity-101/what-is-xdr/
- Benefits
- Consolidated threat visibility: XDR delivers granular visibility by working across multiple layers, collecting and correlating data from email, endpoints, servers, cloud workloads and networks.
- Hassle-free detections and investigation: Analysts and threat hunters can focus on high-priority threats because XDR weeds out anomalies determined to be insignificant from the alert stream. And with advanced analytics and correlation content prebuilt in the tool, XDR automatically detects stealthy threats — all but eliminating the need for security teams to spend time constantly writing, tuning, and managing detection rules.
- End-to-end orchestration and response: Detailed, cross-domain threat context and telemetry — from impacted hosts and root cause to indicators and timelines — guides the entire investigation and remediation process. Automated alerts and powerful response actions can trigger complex, multi-tool workflows for dramatic SOC efficiency gains and surgical threat neutralization.
- Advantages over EDR and SIEM
- Provides broader context for threat detection
- Offers more automated response capabilities
- Reduces the complexity of managing multiple security tools
4. MDR (Extended Detection and Response)
- What it is?
- MDR is a cybersecurity service that combines technology with human expertise to rapidly identify and limit the impact of threats by performing threat hunting, monitoring, and response. The main benefit of MDR is that it quickly helps in limiting the impact of threats without the need for additional staffing, which can be costly.
- Managed Security Services Providers (MSSPs) are the predecessors of MDR. MSSPs typically provide broad monitoring of the network for events and send validated alerts to other tools or to the security team, along with a range of other services such as technology management, upgrades, compliance, and vulnerability management, but generally do not actively respond to threats. The customer is responsible for performing those activities, which can require specialized expertise that is not often maintained in-house. As a result, MSSP customers must also engage additional consultants or vendors to perform mitigation and remediation.
- MDR services are tightly focused on detecting and responding to emerging threats quickly. In addition, MDR delivers mitigation and remediation capabilities, and can deliver immediate value with minimal investment.
- History
- MDR can be traced back to the mid-2010s when organizations began to recognize the need for a more comprehensive security solution capable of dealing with the increasing sophistication of cyber threats. According to a report by ResearchAndMarkets.com, the global MDR market is expected to grow from 2.6 billion in 2017 to 5.6 billion by 2027.
- MDR has become an essential service in modern cybersecurity because it provides a proactive approach to threat detection and response, assists organizations in quickly identifying and mitigating threats, provides ongoing monitoring, and responds to cyber threats in real time. It is also a cost-effective solution for organizations because it does not necessitate additional staffing.
- How it works
- Prioritization – Managed prioritization helps organizations that struggle with the daily effort of sifting through their massive volume of alerts determine which to address first. Often referred to as “managed EDR,” managed prioritization applies automated rules and human inspection to distinguish benign events and false positives from true threats. The results are enriched with additional context, and distilled into a stream of high-quality alerts.
- Threat Hunting – Behind every threat is a human being who’s thinking about how to avoid being caught by their targets’ countermeasures. While machines are very smart, machines are not wily: a human mind is needed to add the element that no automated detection system can provide. Human threat hunters with extensive skills and expertise identify and alert on the stealthiest and most evasive threats in order to catch what the layers of automated defenses missed.
- Investigation – Managed investigation services help organizations understand threats faster by enriching security alerts with additional context. Organizations are able to more completely understand what happened, when it happened, who was affected, and how far the attacker went. With that information, they can plan an effective response.
- Guided Response – Guided response delivers actionable advice on the best way to contain and remediate a specific threat. Organizations are advised on activities as fundamental as whether to isolate a system from the network to the most sophisticated, such as how to eliminate a threat or recover from an attack on a step-by-step basis.
- Remediation – The final step in any incident is recovery. If this step is not performed properly, then the organization’s entire investment in its endpoint protection program is wasted. Managed remediation restores systems to their pre-attack state by removing malware, cleaning the registry, ejecting intruders, and removing persistence mechanisms. Managed remediation ensures that the network is returned to a known good state and further compromise is prevented.
5. EDR vs XDR vs MDR
- Below comparison table is from CrowdStrike, EDR vs MDR vs XDR article.

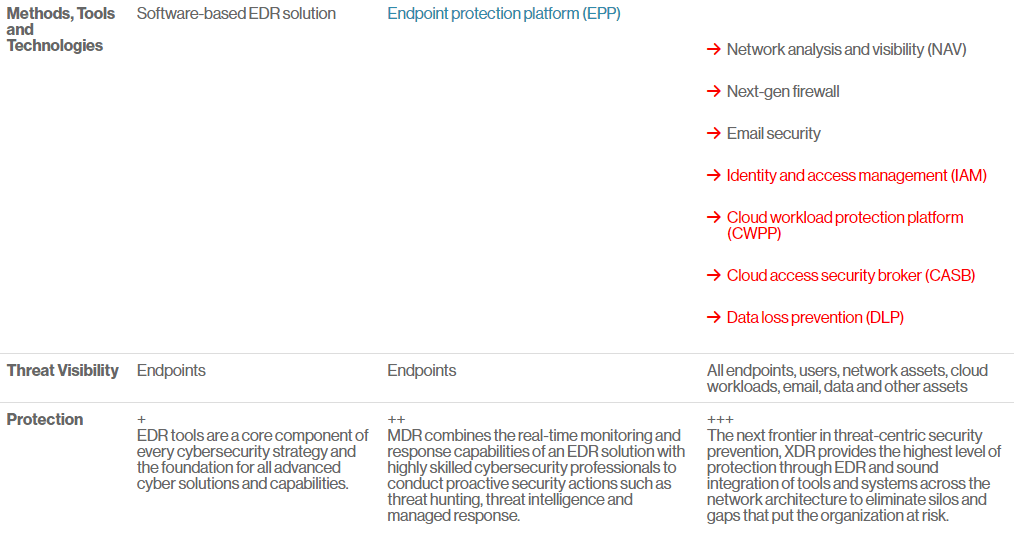
- SentinelOne has excellent EDR vs XDR comparison table outlining various features. Please go to their site to find out more.
6. SOAR (Security Orchestration, Automation and Response)
- What is it?
- Security orchestration, automation and response (SOAR) is a collection of software programs developed to bolster an organization’s cybersecurity posture. A SOAR platform enables a security analyst team to monitor security data from a variety of sources, including security information and management systems and threat intelligence platforms.
- Your security team can increase efficiency and response time by using a SOAR platform. It collects threat information, automates routine responses and triages more complex threats, minimizing the need for human intervention.
- As coined by Gartner, the term SOAR encapsulates three software capabilities:
- Threat and vulnerability management,
- Security incident response, and
- Security operations automation.
- The overall goal of a SOAR platform is to collect threat-related data and automate threat responses.
- A SOAR solution uses both manual human intervention as well as machine learning technology to analyze incoming security data and prioritize incident response actions.
- The first component of SOAR is security orchestration, which enables security tools to work together and communicate to streamline the security process. Compiling this data in one spot allows for a centralized security response.
- The second component, automation, involves completing tasks without human intervention.
- The third component, response, allows your security team to neutralize a threat, using either an automated response or human intervention.
- How it works?
- SOAR solutions work by prioritizing and standardizing incident response activities so that security teams can collaborate on investigating and managing incidents. Workflows that can be handled through automation go through standardized response processes defined in playbooks.
- SOAR platforms vary depending on vendor, but all of them should include these key features:
- Orchestration: A SOAR solution can facilitate the connection between security and productivity tools, such as firewalls and intrusion detection tools. A SOAR system enables cybersecurity and IT teams to combine efforts as they address the overall network environment in a more unified manner. The tools that SOAR uses can combine internal data and external information about threats. Teams can then use this information to ascertain the issues at the root of each security situation.
- Automation: The automation features of SOAR set it apart from other security systems because they help eliminate the need for manual steps, which can be time-consuming and tedious. Security automation can accomplish a wide range of tasks, including managing user access and query logs. Automation can also be used as a tool for orchestration. As an orchestration solution, SOAR can automate tasks that would normally necessitate multiple security tools.
- Response: Both orchestration and automation provide the foundation for the response feature of a SOAR system. With SOAR, an organization can manage, plan, and coordinate how they react to a security threat. The automation feature of SOAR eliminates the risk of human error. This makes responses more accurate and cuts down on the amount of time it takes for security issues to be remedied.
- Integration: A SOAR platform can work with a variety of complementary security products to support the organization’s overall security posture.
- Example SOR playbook, sourced from paloaltonetworks
- SOARs ingest alert data, and these alerts then trigger playbooks that automate/orchestrate response workflows or tasks. Then, using a combination of human and machine learning, organizations are able to analyze this diverse data in order to comprehend and prioritize automated incident response actions to any future threats, thus creating a more efficient and effective approach to handling cybersecurity and improving security operations.

- SOAR use cases
- Go to this link to find out common use cases for SOAR, https://www.paloaltonetworks.com.au/cyberpedia/what-is-soar.
- SOAR Best Practices
- Automated incident response
- An effective SOAR solution should be able to monitor security alerts and respond to them using tools that make automation easy.
- Orchestration
- Tools should link up with each other and act as a group. You’ll also want to make sure your preferred integrations are compatible with your existing environment.
- Threat intelligence
- Many SOAR platforms use threat intelligence to gather contextual data on potentially malicious activity. This helps security teams decide the best course of action for staying protected.
- Robust incident management
- Incidents should be documented, managed, and investigated from one centralized place. This helps identify and manage threats that are both potential and unknown.
- Playbook automation
- When evaluating SOAR solutions, you’ll want to be able to create a variety of playbooks and have access to both pre-built and custom workflows.
- Scalable, flexible infrastructure
- With technology in a constant state of flux, scalability and availability are essential in a SOAR solution. Find a solution that can scale up or down to meet your needs.
- Automated incident response
7. SIEM vs SOAR
- SOAR vs SIEM
- The sole purpose of a SIEM software solution is to collect and send alerts to security personnel to investigate.
- The SOAR tool uses data on security issues to automate the response. SOAR also uses artificial intelligence to predict and respond to similar future threats.
- Below table is populated as per the article from Platoaltonetworks.
| SOAR | SIEM | |
| Focus and Purpose | SOAR platforms primarily focus on automating and orchestrating incident response processes, allowing security teams to respond quickly and efficiently to security incidents and threats. | SIEM systems are designed to collect, correlate, and analyze security event data from various sources to provide insights into potential security issues but offer a different level of automation for incident response. |
| Automation | SOAR solutions offer extensive automation capabilities, enabling the execution of predefined actions and workflows in response to security events or incidents. This automation reduces manual intervention and response time. | SIEM systems provide a different level of automation for incident response. They focus more on data aggregation, correlation, and reporting. |
| Integration | SOAR platforms excel in incident response by providing a war room for incident investigation and collaboration, automating repetitive tasks, orchestrating incident workflows, and enabling security teams to respond rapidly to incidents, reducing mean time to resolution (MTTR). | SIEM systems provide visibility into security events and can generate alerts. Still, they rely on human analysts to investigate, assess, and respond to incidents, which can lead to longer response times. |
| Scalability | SOAR solutions are scalable and adaptable to various security environments, making them suitable for organizations of different sizes. | SIEM solutions can be resource-intensive and may require substantial hardware and software infrastructure for larger organizations. |
| Benefits Refer to https://www.paloaltonetworks.com.au/cyberpedia/what-is-soar-vs-siem for more details. | Enhanced Security Monitoring Through Data Collection and Analysis => Improved Incident Response Times Through Real-Time Alerting => Compliance Adherence Through Advanced Reporting Capabilities => Operational Efficiency Through Automation and Improved Prioritization => Holistic View of Security Posture Through Integration with Other Security Solutions | Improved SOC Efficiency by Automating Incident Response => Responds to Incidents with Speed and at Scale => Ingests, Searches, and Queries All Security Alerts => Facilitates Analyst Collaboration on Investigations => Acts on Threat Intelligence with Agility and Confidence |
7. XSOAR (Extended Security Orchestration, Automation, and Response)
All the contents for XSOAR are from cortex website.
- What it is?
- Cortex XSOAR is the industry’s first extended security orchestration and automation platform that simplifies security operations by unifying automation, case management, real-time collaboration, and threat intel management.
- Cortex XSOAR ingests aggregated alerts and indicators of compromise (IOCs) from detection sources, such as security information and event management (SIEM) solutions, network security tools, threat intelligence feeds, and mailboxes, before executing automatable, process-driven playbooks to enrich and respond to these incidents. These playbooks coordinate across technologies, security teams, and external users for centralized data visibility and action.
- With a Threat Intel Management license, Cortex XSOAR provides a Threat Intelligence Platform with actionable threat data from Unit 42. You can identify and discover new Malware families or campaigns and create and disseminate strategic intelligence reports.
- How Cortex XSOAR works
- Cortex XSOAR ingests aggregated alerts and indicators of compromise (IoCs) from detection sources such as security information and event management (SIEM) solutions, network security tools, threat intelligence feeds, and mailboxes, before executing automatable, process-driven playbooks to enrich and respond to these incidents. These playbooks coordinate across technologies, security teams, and external users for centralized data visibility and action.
- For existing Cortex users, XSOAR is easily integrated into other Cortex solutions and is delivered from the same platform. Cortex XSOAR ingests alerts from third-party products and Threat intel feeds and by installing content packs, you can automate the investigation and response process.
- For managed security services providers (MSSPs), Cortex XSOAR supports full multi-tenancy with data segmentation and scalable architecture. MSSPs can build their managed service operations on Cortex XSOAR to provide best-in-class offerings for their customers and optimize internal team productivity

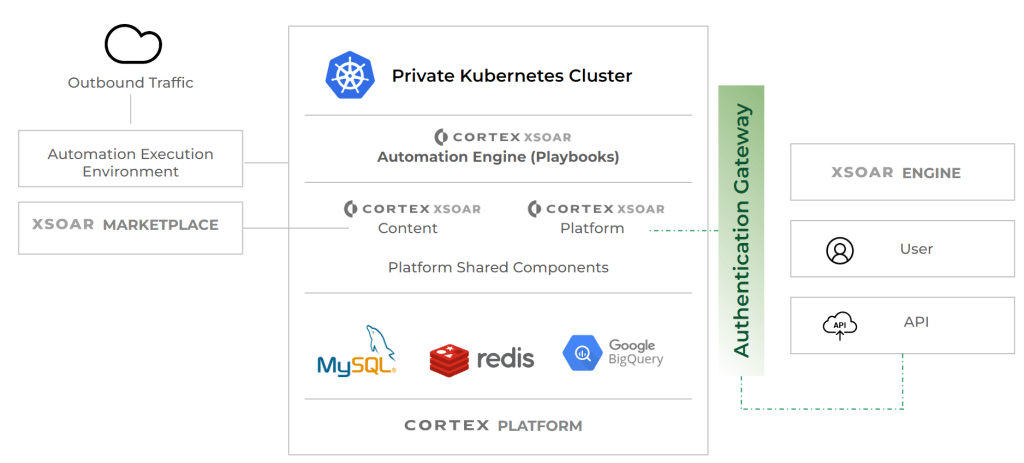
- CORTEX Architecture
- Cortex XSOAR uses the following:
- Rational store using MySQL
- Cache and synchronization using Redis
- Data warehousing using GCP Big Query
- Cortex XSOAR’s playbooks execute on dedicated and isolated workers. Workloads do not share compute resources and there is a scalable API layer. Email and GIT services are included out-of-the-box.
8. XSIAM (Extended Security Intelligence and Automation Management)
Below contents are from Cortex XSIAM Administrator Guide.
- What it is?
- Extended security intelligence and automation management, or XSIAM, is a new approach to security operations that drives dramatically better security outcomes by closely integrating and automating the capabilities and processes of a modern security operations center (SOC).
- How it works?
- XSIAM aims to unify security data, analytics, and automation in a single platform, providing a more comprehensive and efficient approach to security operations.
- Key capabilities
- Security Information and Event Management (SIEM)
- Delivers all common SIEM functions, including log management, correlation and alerting, reporting, and long-term data retention.
- Threat Intelligence Platform (TIP)
- Aggregates, scores, and distributes threat intelligence data, including the industry-leading Unit 42® threat feed, to third-party tools and enriches alerts for context and attribution.
- Extended Detection and Response (XDR)
- Gathers telemetry from any source for unrivaled detection coverage and accuracy, with the highest number of technique-level detections in the 2022 MITRE ATT&CK evaluations.
- Endpoint Protection Platform (EPP)
- Prevents endpoint attacks with a proven endpoint agent that blocks exploits, malware, and fileless attacks and collects full telemetry for detection and response.
- Attack Surface Management (ASM)
- Provides embedded attack surface management (ASM) capabilities for an attacker’s view of your organization, with asset discovery, vulnerability assessment, and risk management.
- Identity Threat Detection and Response (ITDR)
- Uses machine learning and behavioral analysis to profile users and entities and alert on behaviors that may indicate a compromised account or malicious insider.
- Security Orchestration, Automation, and Response (SOAR)
- Automates nearly any use case with hundreds of built-in playbooks and offers customization with a visual drag-and-drop playbook editor.
- Cloud Detection and Response (CDR)
- Analyzes cloud audit, flow, and container host logs together with data from other sources for holistic detection and response across your hybrid enterprise.
- Management, Reporting, and Compliance
- Simplifies operations, centralizing all configuration, monitoring, and reporting functions, including endpoint policy management, orchestration, and response.
- Security Information and Event Management (SIEM)
- Cortex XSIAM Architecture
9. Miscellaneous
- Network Detection and Response (NDR): Monitors communications within the network to detect, investigate and respond to threats that might otherwise remain hidden in unmanaged devices across on-premises, cloud and hybrid environments.
- Identity Threat Detection and Response (ITDR): Detects threats to all Service and Privileged accounts on your network and cloud.
- Managed Extended Detection and Response (MXDR): Delivers managed multi-domain protection with 24/7 dedicated support, expertise, and response.
Summary
I hope that this blog post gives you a glimpse of the evolution of various cybersecurity technologies, starting with SIEM and progressing to advanced platforms like XSOAR and XSIAM used in various organizations. Understanding these technologies is crucial for cybersecurity professionals and organizations striving to stay ahead of evolving threats.
AI and automation have revolutionized the way we work, and they have also had a crucial impact on the security field. As evidenced by newer platforms such as XSOAR and XSIAM, these technologies are reducing manual workloads for SOC analysts, threat hunters, red and blue teams, improving response times, and enhancing the ability to detect sophisticated threats across large, complex environments.
While these advanced technologies offer powerful capabilities, the organizations still require skilled SOC analyst, Security Engineer, Platform Engineer, Detection Engineer, Pen Tester, etc. to implement, manage, and interpret their outputs effectively and prevent the attacks. As cyber threats continue to evolve, so are the innovations incorporating more advanced AI and machine learning techniques to technologies. It is a very interesting and exciting industry to be in to learn and grow!
Below is a summary of each technology discussed in the blog post.
- SIEM (Security Information and Event Management)
- SIEM is a set of tools and services that combine security events management (SEM) and security information management (SIM) capabilities that helps organizations recognize potential security threats and vulnerabilities before business disruptions occur. SIM focuses on collecting and managing logs and other security data while SEM involves real-time analysis and reporting.
- EDR (Endpoint Detection and Response)
- EDR continuously monitors endpoints (desktops, laptops, servers, or any device connected to an organization’s network) to detect malicious behavior or malware. As the name implies, EDR systems help users respond to threats; with some tools, this process is automated.
- XDR (Extended Detection and Response)
- Extended detection and response (XDR) collects threat data from previously siloed security tools across an organization’s technology stack for easier and faster investigation, threat hunting, and response. An XDR platform can collect security telemetry from endpoints, cloud workloads, network email, and more. Gartner defines XDR as a “unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.”
- MDR (Managed Detection and Response)
- MDR is a cybersecurity service that combines technology with human expertise to rapidly identify and limit the impact of threats by performing threat hunting, monitoring, and response. The main benefit of MDR is that it quickly helps in limiting the impact of threats without the need for additional staffing, which can be costly.
- SOAR (Security Orchestration, Automation and Response)
- Security orchestration, automation and response (SOAR) is a collection of software programs developed to bolster an organization’s cybersecurity posture. A SOAR platform enables a security analyst team to monitor security data from a variety of sources, including security information and management systems and threat intelligence platforms.
- As coined by Gartner, the term SOAR encapsulates three software capabilities:
- Threat and vulnerability management,
- Security incident response, and
- Security operations automation.
- XSOAR (Extended Security Orchestration, Automation, and Response)
- Cortex XSOAR is the industry’s first extended security orchestration and automation platform that simplifies security operations by unifying automation, case management, real-time collaboration, and threat intel management.
- Cortex XSOAR ingests aggregated alerts and indicators of compromise (IOCs) from detection sources, such as security information and event management (SIEM) solutions, network security tools, threat intelligence feeds, and mailboxes, before executing automatable, process-driven playbooks to enrich and respond to these incidents. These playbooks coordinate across technologies, security teams, and external users for centralized data visibility and action.
- XSIAM (Extended Security Intelligence and Automation Management)
- Extended security intelligence and automation management, or XSIAM, is a new approach to security operations that drives dramatically better security outcomes by closely integrating and automating the capabilities and processes of a modern security operations center (SOC).
- XSIAM aims to unify security data, analytics, and automation in a single platform, providing a more comprehensive and efficient approach to security operations.
References
- Managed Detection and Response (MDR), Nick Hayes, Jan 17 2024, https://www.crowdstrike.com/cybersecurity-101/managed-detection-and-response-mdr/
- What is Cortex SOAR?, https://docs-cortex.paloaltonetworks.com/r/Cortex-XSOAR/8/Cortex-XSOAR-Cloud-Documentation/What-is-Cortex-XSOAR
- What is Endpoint Detection and Response (EDR)?,Anne Aarness, Oct 26 2023, https://www.crowdstrike.com/cybersecurity-101/endpoint-security/endpoint-detection-and-response-edr/
- What is Endpoint Detection and Response (EDR)?, https://www.paloaltonetworks.com.au/cyberpedia/what-is-endpoint-detection-and-response-edr
- What Is Security Information and Event Management (SIEM)?, Arfan Sharif, Sep 8 2023, https://www.crowdstrike.com/cybersecurity-101/security-information-and-event-management-siem/
- What is SOAR, https://www.fortinet.com/resources/cyberglossary/what-is-soar
- What is SOAR, https://www.paloaltonetworks.com.au/cyberpedia/what-is-soar
- What is SOAR, https://www.microsoft.com/en-au/security/business/security-101/what-is-soar
- What is XDR?, Anne Aarness, Apr 18 2023, https://www.crowdstrike.com/cybersecurity-101/what-is-xdr/
- XDR vs SIEM vs SOAR, Anne Aarness, Mar 10 2022, https://www.crowdstrike.com/cybersecurity-101/what-is-xdr/xdr-vs-siem-vs-soar/


Leave a comment