Introduction to Hashing in Cybersecurity
By suktech24, Sun 20 Oct 2024, Estimated reading time : 12-14 mins
Hashing is a fundamental concept in cybersecurity, playing a pivotal role in securing/protecting sensitive data, identifying malware, enhancing threat detection. In this blog post, the following topics will be explored:
- What is Cryptography and Hashing?
- 1.1 Cryptography
- 1.2 Hashing
- How Hashing Works: The Process
- Types of Hashing Algorithms
- 3.1. Characteristics of Hashing Algorithms
- 3.2. Calculate file hash in Windows
- Use Cases for Hashing in Cybersecurity
- Hash Cracking and Password Hashing
- Indicators of Compromise (IOCs)
- Example of IOC with SHA-256 Hash
- 7.1 File Hash IOC with SHA-256 Hash
- 7.2 User password hash without salt
- Benefits of Hashes in Threat Detection and Hunting
1. What is Cryptography and Hashing?
1.1 Cryptography
Cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. The word is a hybrid of two Greek words: “kryptós”, which means hidden, and “graphein”, which means to write. Literally, the word cryptography translates to hidden writing. The format makes it unreadable for unauthorized users. The four main principles of cryptography are:
- Confidentiality – only the intended recipient can access and read the information, no one else
- Integrity – encoded data cannot be modified or tampered with in transit
- Authenticity – identities and destinations are verified
- Non-repudiation – sender is accountable for their messages since they cannot deny that the message was transmitted – e.g. digital signatures and email tracking
Cryptography field is very broad and has many different types of cryptography algorithms which can be applied in different use cases that require varying levels of security and types of information to be transmitted. There are three main cryptography:
- Symmetric Key Cryptography
- Symmetric key cryptography uses a shared single key for both encryption and decryption. In symmetric cryptography, both the sender and receiver of an encrypted message will have access to the same secret key.
- Encryption process is comparatively fast and efficient and requires fewer resources compared to asymmetric encryption.
- Examples
- Data Encryption Standard – DES
- Advanced Encryption Standard – AES
- Asymmetric Key Cryptography
- Asymmetric cryptography (also referred to as public key cryptography) uses one private key and one public key. Data that is encrypted with a public and private key requires both the public key and the recipient’s private key to be decrypted.
- Public key cryptography enables secure key exchange over an insecure medium without the need to share a secret decryption key because the public key is only used in the encryption, but not the decryption process. In this way, asymmetric encryption adds an additional layer of security because an individual’s private key is never shared.
- It is more secure and robust compared to symmetric encryption, but resource intensive.
- Examples
- RSA algorithm

Sourced from, https://www.researchgate.net/figure/Symmetric-and-Asymmetric-key-Cryptography-Scheme-In-a-symmetric-key-there-are-two-types_fig1_341980135
- Hash Functions
- This cryptography does not involve use of keys like above two. Instead, a hash value—a number of fixed lengths that acts as a unique data identifier—is created based on the length of the plain text information and used to encrypt the data.
Cryptography is an essential cybersecurity tool since the use of cryptography ensures data and users are protected. There are many use cases for cryptography. Some are:
- Passwords – validate password authenticity
- Secure web browsing – secure socket layer (SSL) and transport layer security (TLS) protocols rely on public key cryptography to protect data sent between web server and client and establish secure communication channels
- Electronic signatures – e-signatures are created by cryptography. They can be validated to prevent fraud and forgeries
- Secure communication – end to end encryption such as WhatsApp 📲
- Authentication – verify a user’s identity and authenticate their access privileges – logging to accounts such as bank account
- Cryptocurrency
1.2. Hashing
Hashing is a one-way mathematical function that turns data into a string of nondescript text (a hash value or hash digest or message digest) that cannot be reversed or decoded. As per Wikipedia, A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptographic application.
Since hashing is one-way, meaning it’s impossible (or extremely difficult) to reverse the process and retrieve the original input from the hash value. This is what makes hashing particularly useful in ensuring data integrity, securing sensitive information, and detecting unauthorized changes.
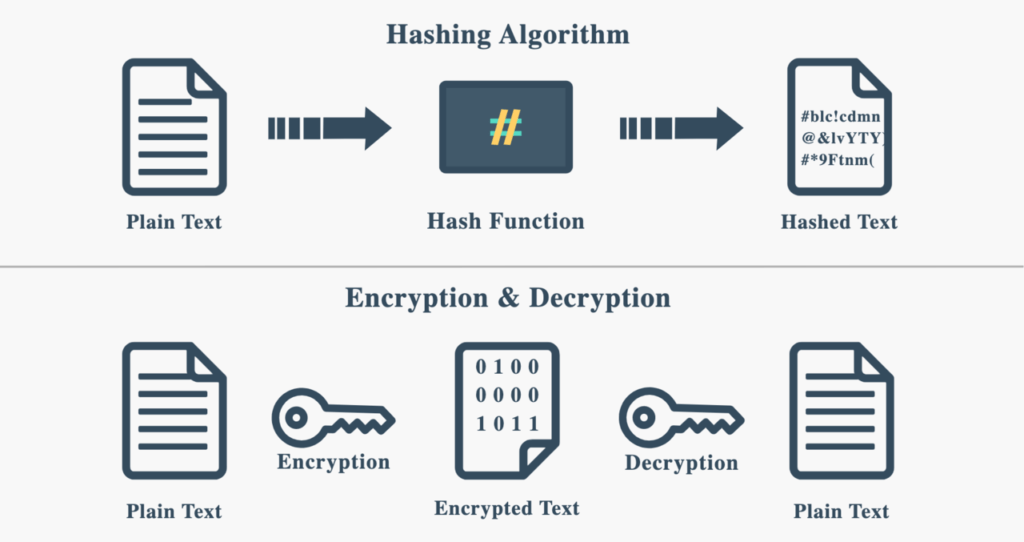
Sourced from, https://arksolvers.com/what-is-hashing-in-cyber-security/
2. How Hashing Works: The Process
The process of hashing begins with taking input data (a file, password, or message), applying a hashing algorithm, and generating a fixed-size output in hexadecimal form. No matter the size of the input, the output (hash) will always have the same length.
For example, in the case of the SHA-256 algorithm, the output will always be 256 bits, regardless of whether you hash a short word or an entire document. A small change in input such as below drastically changes the output (digest). This is called the avalanche effect which is a very desirable effect.

Sourced from Wikipedia, https://en.wikipedia.org/wiki/Cryptographic_hash_function
3. Types of Hashing Algorithms
3.1. Characteristics of Hashing Algorithms
Before diving into hashing algorithms, let’s have a look at some key characteristics of hashing algorithms:
- Deterministic : The same input will always generate the same hash value
- Non-reversible : It is practically impossible to determine the original input from the hash value, a process known as a preimage attack.
- Collision resistant : It is extremely difficult to find two different inputs that give the same hash value, known as a collision attack.
- Avalanche effect: A small change in the input results in significant changes to the hash value.
There are several Secure Hashing Algorithms (SHA) used in cybersecurity. Below is the SHA functions comparisons.
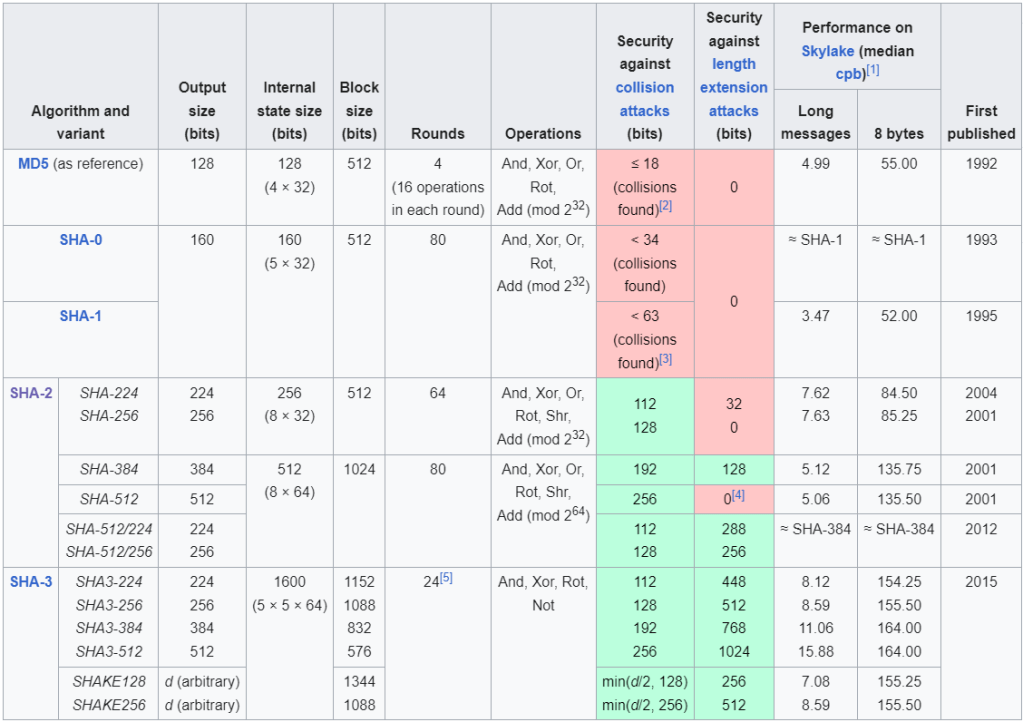
Sourced from, https://en.wikipedia.org/wiki/Secure_Hash_Algorithms
Some of the most common ones include:
- MD5 (Message Digest Algorithm 5): Once widely used, MD5 produces a 128-bit hash. However, extensive vulnerabilities have been found related to collision resistance, allowing unauthorized parties to create files with matching hashes. This led to MD5 being deemed insecure for most cryptographic purposes.
- SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm. Cryptographic weaknesses were discovered in SHA-1, and the standard was no longer approved for most cryptographic uses after 2010.
- SHA-2: A family of two similar hash functions, with different block sizes, known as SHA-256 and SHA-512. They differ in the word size;
- SHA-256 uses 32-bit words
- SHA-512 uses 64-bit words
- SHA-256 (Secure Hash Algorithm 256-bit): Part of the SHA-2 family, SHA-256 produces a 256-bit hash and is widely used in securing digital signatures and certificates due to its robust security properties.
Other notable hashing algorithms include SHA-512 and newer variations in the SHA-3 family.
For overview, go to this page, https://en.wikipedia.org/wiki/Secure_Hash_Algorithms.
3.2. Calculate file hash in Windows
You can use Powershell’s build in Get-FileHash cmdlet to get the file hash value.
- Create a text file called hello_world.txt and type `hello world` and run
Get-FileHash hello_world.txt- Modify
hello Worldand run it again.
You will find that file hash values are different. By default, it uses the SHA-256 algorithm.

4. Use Cases for Hashing in Cybersecurity
In cybersecurity, hashing has several crucial use cases, including:
- Data File Integrity Verification: Hashing is used to verify that files have not been altered. By comparing the hash of a file with a previously calculated hash, security professionals can confirm whether a file has been modified.
- Password Storage: Instead of storing plain-text passwords, systems hash passwords before storing them in databases. When a user logs in, their password is hashed and compared to the stored hash for authentication. Techniques like “salting” (adding random data to passwords) further enhance security.
- Digital Signatures: Hashing is used in the process of generating digital signatures, ensuring the integrity and authenticity of messages and documents.
- Malware Detection: Hashes can be calculated for malware samples, creating unique identifiers for each known threat. These hashes are stored in malware databases and used for detecting malicious files during system scans.
5. Hash Cracking and Password Hashing
Although the hashing algorithms cannot be reversed, password hashes could be cracked. Hackers can generate hashes from a dictionary of strings that are commonly used as passwords.
- Brute force dictionary attack : If hackers gain access to a database of hashed passwords, they can calculate the hash code for each string in the database and match it with the current hash code. If one in the database matches, the plaintext password of that hash is known. This is called brute force dictionary attack. It is very time-consuming for calculating the hash code for every string in the database.
- Rainbow table attack : A rainbow table is a precomputed set of hash values used to crack password databases that do not store their information as plaintext. These tables allow attackers to access secure systems without guessing a password. The attacker first creates a “chain” of hash values to generate a rainbow table. Rainbow refers to the different colors used in the table to show the various hashing and reduction functions and steps. With each reduction function being a different color, the final plaintexts and hashes would look like a rainbow. Rainbow tables are a listing of the password hash values for each plaintext character used during authentication. Threat actors could either make a large list of hashes that correlate to common passwords or gain access to a list of password hashes.
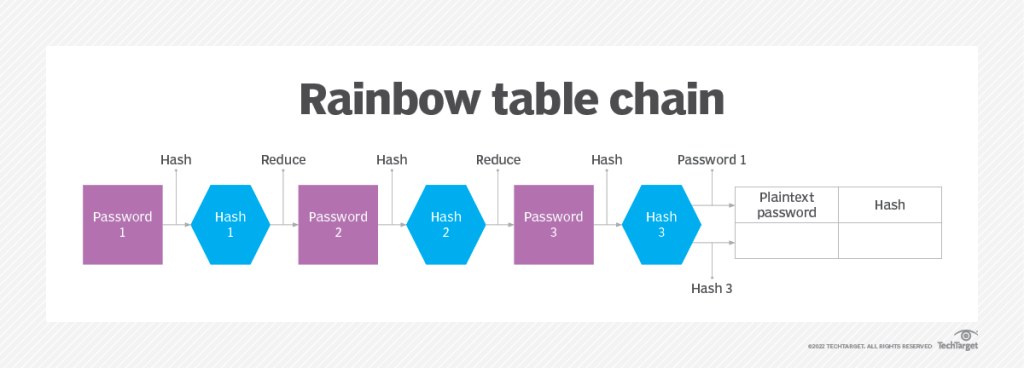
Sourced from, https://www.techtarget.com/whatis/definition/rainbow-table
- To crack a password, or for rainbow table attacks, large numbers of hashes are run through a dataset and then through multiple reduction stages to split them into smaller components that are linked to plaintext characters. The plaintext passwords are then stored in the table next to their hashes.
- A password-cracking program then compares the rainbow table’s list of potential hashes to hashed passwords in the database. If there’s a match, the plaintext that produced the hash is retrieved and the process is stopped. With the correct hash, the threat actor can now successfully access the device — they’ve cracked the authentication process.
- To protect against attacks such as rainbow tables, the following security measures could be applied:
- Salting (adding a random value to the input before hashing) are used to defend against such attacks. Go to CVE-2024-38881 to find out more, https://nvd.nist.gov/vuln/detail/CVE-2024-38881
- Biometric authentication
- Good password hygiene
- Multi-Factor authentication
- Key stretching – password + salt + intermediate hash values are run through a hash function multiple times to increase the computation time for the attack
Properly implemented hashing with strong algorithms like SHA-256 and salting makes it exceedingly difficult for attackers to crack hashes, even with sophisticated techniques.
6. Indicators of Compromise (IOCs)
In threat detection and cybersecurity, Indicators of Compromise (IOCs) are important evidence that suggest a security breach or malicious activity has occurred. IOCs can take various forms, including:
- File hashes: Unique hash values of malicious files.
- IP addresses: Known malicious IP addresses associated with malware.
- Domain names: Domains used by attackers for phishing or malware distribution.
- Registry changes: Changes in system registry that indicate potential compromise.
File hashes, particularly, are one of the most reliable IOCs as they provide a unique identifier for malware that can be shared and referenced across security systems. When a malware is detected, its hash can be added to Threat intelligence database. For example, antivirus software are capable of detecting a wide range of malicious programs, worms, trojan viruses, new modifications of computer viruses. File hashes are part of the detection process (identifying known malware by ash). They are the first step in the detection process followed by archive extraction and deeper file inspection.
7. CVE and IOC Examples
7.1 File Hash IOC with SHA-256 Hash
Below is an example of IOC hash associated with CVE-2024-21762 and the vulnerability is in Fortinet’s FortiOS and FortiProxy.
Go to https://www.threatintelligence.com/blog/fortinet-custom-iocs for more details.
- MD5: 3a97d9b6f17754dcd38ca7fc89caab04
- SHA-1: ffb1d8ea3039d3d5eb7196d27f5450cac0ea4f34
- SHA-256: eaef901b31b5835035b75302f94fee27288ce46971c6db6221ecbea9ba7ff9d0
- SHA-512: d99941e4445efed5d4e407f91a9e5bba08d1be3f0dab065d1bfb4e70ab48d6526a730233d6889ba58de449f622e6a14e99dab853d40fc30a508627fd2735c973
If you check this hash, `eaef901b31b5835035b75302f94fee27288ce46971c6db6221ecbea9ba7ff9d0`, on website such as Virus Total, it is flagged as malicious.

7.2 User password hash without salt
The bug was discovered 04/06/2024. The weakness was published by Austin Henderson (CerebralStud) with jTag Labs as security advisory (VulDB). The public release has been coordinated with Horizon Business Services. Caterease stores user password hashes without salts, making them vulnerable to rainbow table attacks. This vulnerability arises because the application fails to use a cryptographic salt when hashing passwords. The identification of this vulnerability is CVE-2024-38881 since 06/21/2024. The exploitation is known to be difficult. The attack can only be done within the local network. No form of authentication is needed for a successful exploitation. Technical details are unknown but a private exploit is available. MITRE ATT&CK project uses the attack technique T1110.002 for this issue.
8. Benefits of Hashes in Threat Detection and Hunting
Hashes are invaluable in threat detection and hunting due to their ability to uniquely identify malware, files, or data in a simple, fixed-length format. The benefits of using hashes include:
- Efficiency in Detection: Hashes allow for the quick identification of known malware and compromised files during scans, as they can be compared against blocklists in antivirus databases.
- Threat Intelligence hash feeds can be updated.
- Standardized Exchange of IOCs: Security researchers and teams can easily share IOCs in the form of file hashes, making it easier to identify and mitigate threats across different systems.
Summary
Hashing remains a vital component of modern cybersecurity strategies, ensuring data integrity, securing sensitive data, identifying malware and enhancing the detection of malicious activities. Below are summary of this blog post.
🍃 1. What is Cryptography and Hashing?
- Cryptography secures communication through techniques like Symmetric and Asymmetric encryption.
- Hashing is a one-way function that transforms data into a fixed-length string, ensuring data integrity and detecting changes.
🍃 2. How Hashing Works: The Process
- The hashing process converts data into a fixed-size hexadecimal output, ensuring even small input changes create drastically different outputs (avalanche effect).
🍃 3. Types of Hashing Algorithms
- Common algorithms include MD5, SHA-1, and SHA-256, each with unique properties and security strengths.
🍃 4. Use Cases for Hashing in Cybersecurity
- Ensures data file integrity, secures password storage, enables digital signatures, and detects malware through unique hash values.
🍃 5. Hash Cracking and Password Hashing
- Despite hashing being one-way, hackers can attempt cracking through techniques like brute force and rainbow table attacks.bDefenses include salting, key stretching, and strong password hygiene.
🍃 6. Indicators of Compromise (IOCs)
- File hashes, IP addresses, and registry changes serve as critical indicators of malware or security breaches.
🍃 7. Example of IOC with SHA-256 Hash
- IOC hash associated with CVE-2024-21762 and the vulnerability is in Fortinet’s FortiOS and FortiProxy.
- CVE-2024-38881 – An issue in Horizon Business Services Inc. Caterease 16.0.1.1663 through 24.0.1.2405 and possibly later versions, allows a remote attacker to perform a Rainbow Table Password cracking attack due to the use of one-way hashes without salts when storing user passwords., https://nvd.nist.gov/vuln/detail/CVE-2024-38881
🍃 8. Benefits of Hashes in Threat Detection and Hunting
- Hashes provide a unique identifier for files, aiding in malware detection, threat intelligence sharing, and more effective security responses.


Leave a comment