Weekly #8-2025 – By suktech24, Sun 30 March 2025, Estimated reading time : 4 mins
In this week blog post, I shifted gear from usual case studies to explore about the MITRE ATT&CK navigator. As a threat detection engineer or analyst, you likely spending time standardizing raw logs, parsing, onboarding new log sources, developing detection use cases (Sigma rule , yara rule, custom specific or based on current CVE or exploits), tuning them ( if SOC being flooded with False Positive alerts or False negative ), and reviewing their effectiveness. But have you ever wondered :
- What attack techniques do your detections actually cover at a high level ( not at each device)?
- What are the gaps in your defensive strategies?
- How can you better align detections with adversary behaviors?
The MITRE ATT&CK nagivator helps answering these questions. In this week blog post, I will cover :
- What is MITRE ATT&CK Navigator
- Why we need it?
- How to use it
- Conclusion
- Further readings ( Highly recommended)
1. What is MITRE ATT&CK Navigator
According to its’s official github repo,
The ATT&CK Navigator is designed to provide basic navigation and annotation of ATT&CK matrices. It is simple and generic – you can use the Navigator to visualize your defensive coverage, your red/blue team planning, the frequency of detected techniques or anything else you want to do. The Navigator doesn’t care – it just allows you to manipulate the cells in the matrix (color coding, adding a comment, assigning a numerical value, etc.). We thought having a simple tool that everyone could use to visualize the matrix would help make it easy to use ATT&CK.
The principal feature of the Navigator is the ability for users to define layers – custom views of the ATT&CK knowledge base :
- Showing just those techniques for a particular platform
- Highlighting techniques a specific adversary has been known to use.
Layers can be created interactively within the Navigator or generated programmatically and then visualized via the Navigator.
NOTE : If you are not familiar with MITRE ATT&CK framework, Paloalto has an excellent blog post introducing the fundamentals of what MITRE ATT&CK is.
2. Why do we need it?
Threat detection professionals onboard logs, parse and standardize fields, and develop detection use cases based on available data. These detections include MITRE ATT&CK tactics and techniques.
The MITRE ATT&CK navigator enable you to identify the tactics and techniques used by adversaries. It helps visualize the bigger picture, benefiting various cybersecurity teams:
- Cyber Threat Intelligence (CTI): Share adversary TTPs visually.
- Blue Teams / Detection Engineers: Identify coverage gaps and prioritize detections.
- DFIR Teams: Map observed behaviors to ATT&CK techniques during investigations.
- Red Teams: Plan adversary emulations and assess detection efficacy. During pen test, firing certain detections confirm coverage – while missed alerts ( where it should have been fired) reveal gap to address.
By leveraging the ATT&CK Navigator, teams can ensure threat-informed defense strategies and improve their overall security posture.
3. How to use it
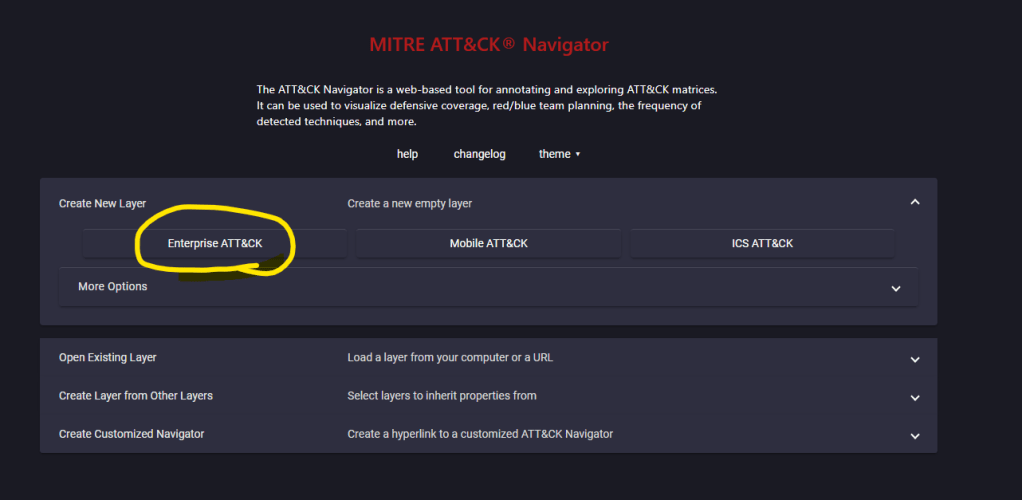
- Visit the site, https://mitre-attack.github.io/attack-navigator/.
- Create a new layer, select the matrix (Enterprise, Mobile, ICS) that you want to analyze
- Start mapping, use colors, add score, etc (e.g. green for covered, red for gaps, orange for could be improved, etc)!
For a step by step walkthrough, please check out, The ATT&CK Navigator: A Powerful Tool for Visualizing Cyber Attacks by Adam Goss.
Every organisations ( big or small, geolocations, private, government) face distinct threats- some common, others highly specialised. To tailor defenses:
- Review your environment ( even better shift left – incorporate secure design when you plan!) : Services, softwares, business domains, third party SaaS dependencies, and architecture blueprint, etc.
- Identify threat vectors : Map them to MITRE ATT&CK TT using navigator
- Priortise detections : Focus on gaps relevant to your orgs
4. Conclusion
I hope that this blog post convinces you to incorporate MITRE ATT&CK techniques correctly when developing detection use cases and that the navigator isn’t just a vistualization tool- but it is a valuable asset for threat-informed decision making.
If you are still not convinced of this tool’s value, let this f5’s comparision of Dridex and Zeus Panda banking trojans demonstrate its power. Below diagram illustrates the unique adversary behaviours, how different threat actors operate , how to tailor defensive strategies accordingly thereby mitigating risks.

Further readings
For deeper dive, I highly recommend Lennart Erikson’s two parts medium blog posts, Three ways to use the ATT&CK Navigator for threat-informed decision making — Part 1 & 2. They are both truly informative. 💡Happy detecting, hunting, and may our detections be effective!
- Three ways to use the ATT&CK Navigator for threat-informed decision making — Part 1, Lennart Erikson, https://medium.com/@lerikson/three-ways-to-use-the-att-ck-navigator-for-threat-informed-decision-making-part-1-65c0c6004df9
- Three ways to use the ATT&CK Navigator for threat-informed decision making — Part 2, https://medium.com/@lerikson/three-ways-to-use-the-att-ck-navigator-for-threat-informed-decision-making-part-2-af6519db384c

Leave a comment