Weekly #9-2025 – By suktech24, Fri 27 June 2025, Estimated reading time : 8 mins
When I first started as a threat detection analyst, I found creating detection use cases quite challenging – I wasn’t sure where to begin. Over time, through trial and error, learning from colleagues, reading blog posts, listening to podcasts like Detection Dispatch , and learning from the generous knowledge sharing from the security community in SubStack and Medium, I picked up a number of useful tips. In this article, I’ll share a practical checklist. It’s designed to help junior detection engineers and analysts build high-quality detection use cases, based on lessons I’ve learned and the resources listed in the references.
Threat Detection Use Case Development Checklist
- Understand the technology and environment
- Under what is normal and what is abnormal
- Research Existing Use Cases and leverage them
- Collect and Validate logs
- Draft Detection Logic in a Reusable Format ( Sigma or Yara)
- Validate in Dev/Test Environment
- Peer Review and Stakeholder Feedback
- Deploy to Production
- Maintain and Improve Continuously
Threat Detection Use Case Development Checklist
- 0. What is Detection Engineering?
- Before diving into the checklist, if you’re new to threat detection engineering or want to refresh your understanding, it’s helpful to revisit some foundational concepts:
- What is Detection Engineering?
- Detection Engineering Lifecycle
- Detection Engineering Maturity Models
- These topics provide a high-level overview of how detection use cases fit into a broader strategy — from identifying gaps and developing detection logic, to testing, deploying, and continuously improving it. Understanding these core concepts will give you better context and help you align your detection use cases work with long-term detection goals and organizational security objectives. Check out below articles.
- Detection Engineering Explained, https://www.splunk.com/en_us/blog/learn/detection-engineering.html
- What Is Detection Engineering?, Oleksandra Rumiantseva, July 14 2023, https://socprime.com/blog/what-is-detection-engineering/
- Detection Engineering Maturity Matrix, Kyle Bailey, https://detectionengineering.io/
- Detection Engineering Maturity Matrix, Kyle Bailey, Apr 26, 2021, https://kyle-bailey.medium.com/detection-engineering-maturity-matrix-f4f3181a5cc7
- What Makes a “Good” Detection?, The Shannon Signal Score: A Framework for Measuring Detection Value, Dylan, Oct 11 2024, https://medium.com/@dylanhwilliams/what-makes-a-good-detection-dd6a3b373860
- What Makes a “Good” Detection, Ryan G. Cox, Dec 04, 2024, https://www.cyberseccafe.com/p/what-makes-a-good-detection
- About Detection Engineering, Florian Roth, Sep 12 2022, https://cyb3rops.medium.com/about-detection-engineering-44d39e0755f0
- Before diving into the checklist, if you’re new to threat detection engineering or want to refresh your understanding, it’s helpful to revisit some foundational concepts:
- Understand the technology and environment
- *** You cannot detect what you don’t understand. ***
- Identify the technology or service you’re working with. If you’re unfamiliar with it, take the time to research and learn it thoroughly.
- Understand how it is used within your organization. Go through company sharing pages ( Confluence, slack, teams, sharepoint, etc), GitHub, GitLab repos and understand how it is used, deployed. Review code and architecture diagrams.
- Identify deployment context ( cloud, hybrid, on-prem, containerized)
- Map dependencies ( e.g. API flows, authentication, SSO, etc.)
- Where possible, access dev or prod environments and explore hands-on (e.g. AWS Console, Azure Portal, EDR tools, network devices).
- Don’t aim to build a single detection use case yet—this is the exploratory phase. Your goal is to map out the broader threat landscape and usage context.
- Research any related CVE e.g. https://www.cve.org/CVERecord?id=CVE-2025-0693
- Find out if there is any Proof of Concept (PoC) exploit for related CVE e.g. https://github.com/trickest/cve, https://digital.nhs.uk/cyber-alerts/2025/cc-4598
- Check threat feeds
- For example, you want to develop use cases for AWS IAM Roles Anywhere.
- Start by reviewing the AWS IAM Roles Anywhere User guide and go through all sections. , https://docs.aws.amazon.com/rolesanywhere/latest/userguide/introduction.html
- Supplement your understanding with credible external resources like this, https://unit42.paloaltonetworks.com/aws-roles-anywhere/
- Then explore how attackers can abuse this role for persistence, How Attackers Can Abuse IAM Roles Anywhere for Persistent AWS Access, https://medium.com/@adan.alvarez/how-attackers-can-abuse-iam-roles-anywhere-for-persistent-aws-access-b3ced6935dca
- Under what is normal and what is abnormal
- *** Start by understanding what normal looks like, then look for deviations. ***
- Based on your research in Step-1, you will have a good understanding of expected normal flow. Map them out.
- Create a simple flow diagram (It does not have to be a fancy one. Just text and arrow are fine).
- Define what behavior would be considered malicious or abnormal. And mark those points on the flow diagram. These will be your detection opportunities.
- Use either MITRE ATT&CK tactics/techniques or Cyber Kill Chain and map threat scenarios and attack surfaces. I use MITRE ATT&CK tactics/techniques. They are useful for aligning detections with adversary techniques.
- If you uncover more than one potential use cases, map attack surface, entry points, etc. for each use case.
- Research Existing Use Cases and leverage them
- *** Don’t reinvent the wheel—leverage open content and industry knowledge ***
- Search if there is already detection use case developed
- Check below sites to get started
- Azure-Sentinel, https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/Amazon%20Web%20Services
- SigmaHQ, https://github.com/SigmaHQ/sigma/tree/master/rules
- ElasticSearch, https://www.elastic.co/guide/en/security/current/prebuilt-rules.html
- SOCPrime, https://socprime.com/
- Google Chronicle Detection Rules, https://github.com/chronicle/detection-rules/tree/main/rules
- Splunk Detection rules, https://github.com/splunk/security_content/tree/develop/detections
- Look for inspiration from blog posts on medium and substack
- When you find similar detections, review and identify the gaps for your use cases
- Collect and Validate logs
- *** Use case quality depends on logging quality ***
- Ensure logs from relevant resources ( e.g. e.g. Windows Security Event logs, Sysmon, Linux syslog/audit) via agents) are ingested.
- At parsing phase, make sure all the relevant fields needed for the detection use cases are correctly parsed/extracted.
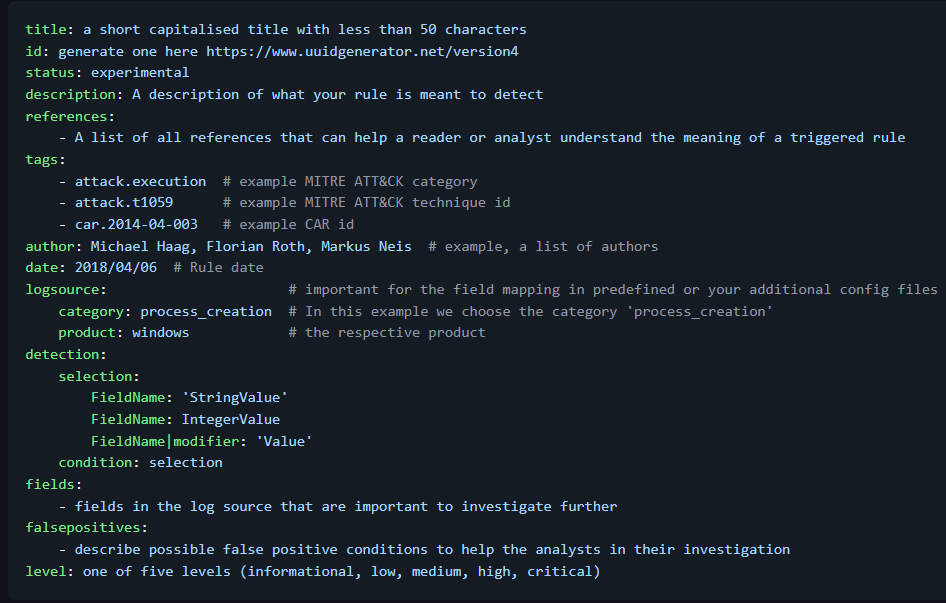
- Draft Detection Logic in a Reusable Format ( Sigma or Yara)
- *** Write once, deploy anywhere ***
- In my experience, it is best to start with drafting detection logic in a reusable format even before translating it into your specific SIEM’s native query language. I recommend Sigma rule , which can be used to be translated into Elasticsearch rule, Splunk, SQL queries or other formats. Sigma rule gives a good starting point. Sigma provides a clean and standardized structure that makes detection logic more shareable, version-controlled, and vendor-agnostic.
- Ideally, detection logic should live in a Detection As Code repo with git control, code reviews, CI/CD pipelines.
- Detection-as-Code is a set of principles that use code and automation to implement and manage threat detection capabilities in an agile Continuous Detection/Continuous Response model.
- To dive deeper into Detection-as-Code, check out these great resources :
- Getting Started with Detection-as-Code and Google SecOps (Part 1 of 2), https://www.googlecloudcommunity.com/gc/Community-Blog/Getting-Started-with-Detection-as-Code-and-Google-SecOps-Part-1/ba-p/702154
- How we use Datadog for detection as code, Oct 11 2024, https://www.datadoghq.com/blog/datadog-detection-as-code/
- What is Detection as Code? How to implement Detection-as-Code, Tahir, Apr 15 2025, https://medium.com/@tahirbalarabe2/what-is-detection-as-code-how-to-implement-detection-as-code-ae8e3bac22f7
- Detection as Code: Key Components, Tools, and More, https://www.legitsecurity.com/aspm-knowledge-base/detection-as-code
- Detection as Code: How To Embed Threat Detection into Code, Muhammad Raza, July 11 2023, https://www.splunk.com/en_us/blog/learn/detection-as-code.html
- When building a sigma rule, organise key information you have gathered under relevant fields/tags
- There are excellent guide and articles that walk through on what Sigma Rule is, how to create step by step. Please read them if you are not familiar with how to create a Sigma Rule.
- SigmaHQ, Rule Create Guide, https://github.com/SigmaHQ/sigma/wiki/Rule-Creation-Guide
- Defender’s Toolkit 102: Sigma Rules, Syed Hasan, Mar 6 2021, https://syedhasan010.medium.com/defenders-toolkit-102-sigma-rules-4a623acb2036
- What Are SIGMA Rules: Beginner’s Guide, Adam Swan, May 16 2022, https://socprime.com/blog/sigma-rules-the-beginners-guide/
- The Ultimate Guide to Sigma Rules, Jeff Darrington, February 18, 2025, https://graylog.org/post/the-ultimate-guide-to-sigma-rules/
- Below is the Rule Template Rule along with explanation.
- There are excellent guide and articles that walk through on what Sigma Rule is, how to create step by step. Please read them if you are not familiar with how to create a Sigma Rule.
- Once your Sigma rule is ready,
- Translate Sigma into SIEM-specific queries ( e.g. Elastic KQL, SQL, Splunk SPL)
- Add enrichment. For example, for SPL, use Macros, Lookup tables, KV store, CIM data models, etc.
- If you are not sure about the logic, seek feedback colleague, work with the product owner.
- Validate in Dev/Test Environment
- *** Your first version is rarely the best. Test and tune repeatedly ***
- Run the detection in a non-production environment for 2 – 5 days. Short duration will not be sufficient to monitor the behavior.
- Ingest test logs to trigger the detection and confirm the logic works as intended.
- Simulate attack scenarios where possible to validate the detection coverage.
- Track detection outcomes
- How many alerts fire?
- Are they True/False positives?
- Tune the logic ( Add conditions, whitelist, blacklist, add thresholds, how the
- Peer Review and Stakeholder Feedback
- *** Feedback from the SOC or Product team is essential for contextual usefulness ***
- Request peer review from fellow threat detection team
- Get input from the SOC team, who will triage the alerts.
- Use a QA checklist for detection use case to standardise reviews.
- If you are reviwer, check for
- Detection logic correctness – Does it accurately capture the intended behavior?
- Noise level – is the threshold acceptable, realistic and actionable?
- Response readiness – How can SOC respond to the detection? SOAR Playbook or manual?
- Once feedback is received, update and re-run the detection if needed.
- Deploy to Production
- *** Production rules need to be stable, documented, and monitored ***
- Move the rule to production after successfully passing both Peer and SOC reviews
- Configure alert routing – e.g. SPLUNK SOAR playbook, email, slack, etc.
- Track the effectiveness of the detection and SOC analysts triage outcomes (true/false positives, actions taken) post deployment
- If needed, tune the detection logic and provide as much context as possible in the ticket for future references.
- Maintain and Improve Continuously
- *** A good detection rule evolves with the environment and the threat landscape ***
- Schedule periodic reviews
- Use Detection engineering metrics to measure efficacy
- FP rate
- True positive rate
- Mean Time to Detect (MTTD)
- Update/Tune rules based on:
- Feedback from SOC
- New threat intel/whitelist, New TTPs, IOC updates
- Product changes e.g. API updates, keywords changes, name changes, etc.
- Deep dive into below resources for Detection Development Lifecycle
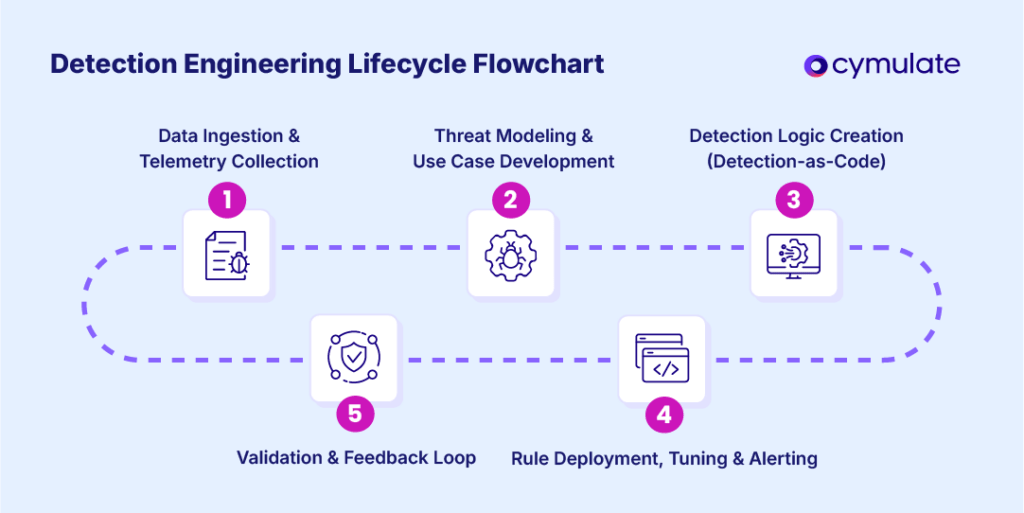
- Sourced from, https://cymulate.com/cybersecurity-glossary/detection-engineering/
- Detection Development Lifecycle, Snowflake’s implementation of the Detection Development Lifecycle, Haider Dost, Jan 19 2022, https://medium.com/snowflake/detection-development-lifecycle-af166fffb3bc
- Elastic releases the Detection Engineering Behavior Maturity Model, Mika Ayenson PHD, Terrance DeJesus, Samir Bousseaden, https://www.elastic.co/security-labs/elastic-releases-debmm
References
- About Detection Engineering, Florian Roth, Sep 12 2022, https://cyb3rops.medium.com/about-detection-engineering-44d39e0755f0
- Awesome-detection-engineering, https://github.com/infosecB/awesome-detection-engineering
- Detection as Code: Key Components, Tools, and More, https://www.legitsecurity.com/aspm-knowledge-base/detection-as-code
- Detection as Code: How To Embed Threat Detection into Code, Muhammad Raza, July 11 2023, https://www.splunk.com/en_us/blog/learn/detection-as-code.html
- Detection Engineering, https://cymulate.com/cybersecurity-glossary/detection-engineering/
- Defender’s Toolkit 102: Sigma Rules, Syed Hasan, Mar 6, 2021, https://syedhasan010.medium.com/defenders-toolkit-102-sigma-rules-4a623acb2036
- Detection Dispatch, https://www.youtube.com/@Anvilogic
- Detection Development Lifecycle, Snowflake’s implementation of the Detection Development Lifecycle, Haider Dost, Jan 19 2022, https://medium.com/snowflake/detection-development-lifecycle-af166fffb3bc
- Detection Engineering Explained, https://www.splunk.com/en_us/blog/learn/detection-engineering.html
- Detection Engineering Maturity Matrix, Kyle Bailey, https://detectionengineering.io/
- Detection Engineering Maturity Matrix, Kyle Bailey, Apr 26, 2021, https://kyle-bailey.medium.com/detection-engineering-maturity-matrix-f4f3181a5cc7
- Elastic releases the Detection Engineering Behavior Maturity Model, Mika Ayenson PHD, Terrance DeJesus, Samir Bousseaden, https://www.elastic.co/security-labs/elastic-releases-debmm
- Getting Started with Detection-as-Code and Google SecOps (Part 1 of 2), https://www.googlecloudcommunity.com/gc/Community-Blog/Getting-Started-with-Detection-as-Code-and-Google-SecOps-Part-1/ba-p/702154
- How we use Datadog for detection as code, Oct 11 2024, https://www.datadoghq.com/blog/datadog-detection-as-code/
- How to Make Threat Detection Better?, Anton Chuvakin, Jul 31 2021, https://medium.com/anton-on-security/how-to-make-threat-detection-better-c38f1758b842
- How to start in creating detection Use Case, Reddit, https://www.reddit.com/r/cybersecurity/comments/jodq0t/how_to_start_in_creating_detection_use_case/
- My first use case, https://cloud.google.com/chronicle/docs/soar/respond/start-developing/my-first-use-case
- Rule Creation Guide, https://github.com/SigmaHQ/sigma/wiki/Rule-Creation-Guide
- SigmaHQ, Rule Create Guide, https://github.com/SigmaHQ/sigma/wiki/Rule-Creation-Guide
- The Ultimate Guide to Sigma Rules, Jeff Darrington, February 18, 2025, https://graylog.org/post/the-ultimate-guide-to-sigma-rules/
- What is your Approach for Building Cyber Threat Use Cases?, July 21 2020, https://www.correlatedsecurity.com/what-is-your-approach-for-building-cyber-threat-use-cases/
- What is Detection as Code? How to implement Detection-as-Code, Tahir, Apr 15 2025, https://medium.com/@tahirbalarabe2/what-is-detection-as-code-how-to-implement-detection-as-code-ae8e3bac22f7
- What Are SIGMA Rules: Beginner’s Guide, Adam Swan, May 16 2022, https://socprime.com/blog/sigma-rules-the-beginners-guide/
- What Is Detection Engineering?, Oleksandra Rumiantseva, July 14 2023, https://socprime.com/blog/what-is-detection-engineering/
- What Makes a “Good” Detection?, The Shannon Signal Score: A Framework for Measuring Detection Value, Dylan, Oct 11 2024, https://medium.com/@dylanhwilliams/what-makes-a-good-detection-dd6a3b373860
- What Makes a “Good” Detection, Ryan G. Cox, Dec 04, 2024, https://www.cyberseccafe.com/p/what-makes-a-good-detection


Leave a comment